Introduction
In recent times, the cybersecurity landscape has witnessed a significant uptick in malicious activities, particularly through email phishing attacks. These attacks often carry malicious payloads, which are ingeniously designed to infiltrate critical infrastructures. The consequence of such breaches is not just limited to system compromises but extends to severe data breaches impacting both individuals and organizations.
Highlighting the gravity of this situation, data from the first quarter of 2021 reveals a disturbing trend. Attack tactics have evolved, with malware campaigns becoming increasingly sophisticated. This evolution in cyberattack strategies has led to a staggering 564 percent increase in the number of individuals affected by data leaks. Additionally, there has been a 12 percent rise in the number of reported breaches. These statistics underscore the pressing need for robust cybersecurity measures to safeguard sensitive information and infrastructure
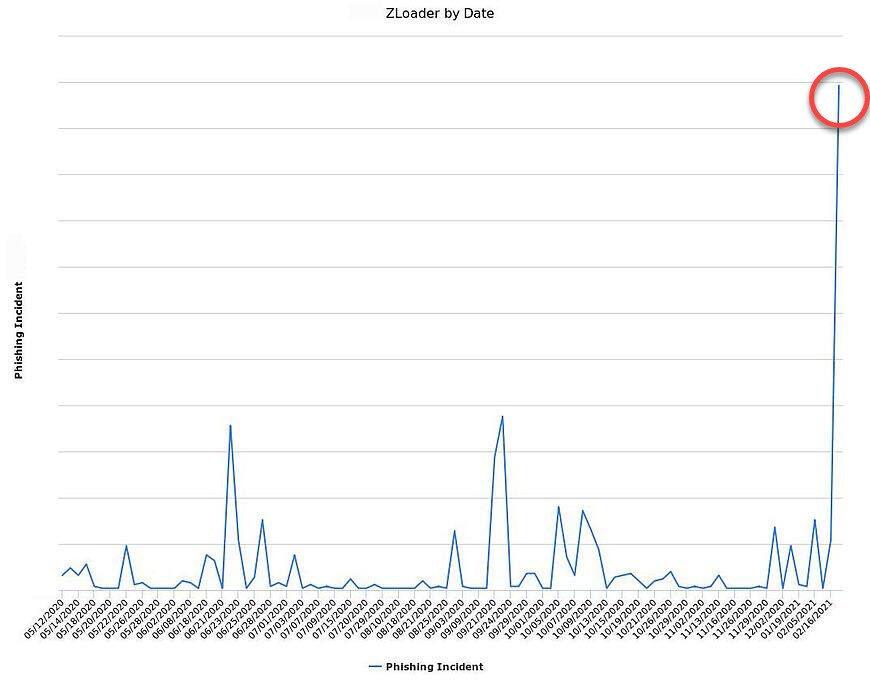
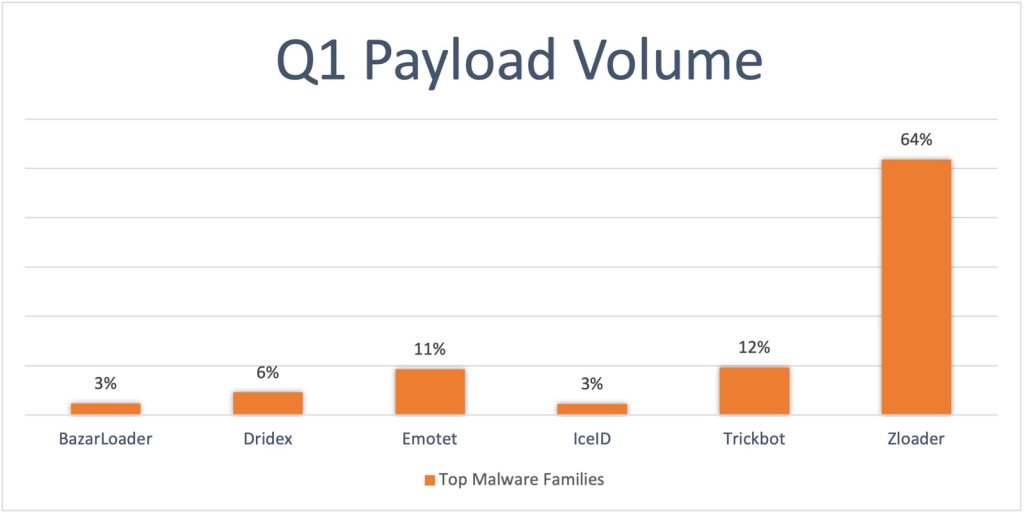
During this period, there was a widespread proliferation of malware attacks via email, with a notable increase in the use of the WeTransfer platform for distributing malware. Numerous hacked accounts were leveraged to send payloads containing malicious software, notably ZLoader, to unsuspecting victims. Once downloaded onto a personal computer, this software would initiate the hacking process. Remarkably, infections involving ZLoader accounted for approximately 65 percent of all reported attacks involving malicious payloads.
What is ZLoader malware
ZLoader malware is a notorious banking Trojan that gained widespread notoriety during the COVID-19 pandemic, despite its initial discovery in 2011. This malicious software is designed to steal banking credentials from its victims. The wave of ZLoader attacks began in Canada in early 2020 and rapidly expanded across the globe, targeting financial institutions in the United States, Australia, Europe, and other regions. Its primary aim is to siphon off victims’ bank credits, posing a significant threat to individual and organizational financial security.
How ZLoader works
ZLoader malware employs a cunning strategy to pilfer banking information from its victims. It begins by monitoring the victim’s internet browser to collect banking data. The malware then utilizes Web injection technology to create a facade, tricking victims into believing they are accessing their genuine banking website. In reality, ZLoader replaces the legitimate site with a counterfeit version hosted on a server controlled by the attacker. Unwitting victims, thinking they are securely logging into their accounts, inadvertently enter their credentials and authentication codes, which are then transmitted directly to the attacker.
Beyond capturing login details, ZLoader is also capable of extracting additional information from browsers, such as cookies and passwords. This capability is a hallmark of banking Trojans, making them particularly effective at accessing a wide range of sensitive data.
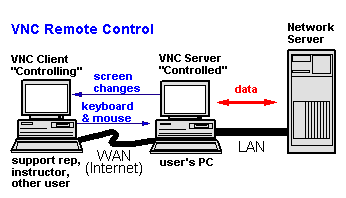
One of the most intriguing aspects of ZLoader’s operation is its ability to evade detection by financial institutions. The attacker can remotely access the victim’s account using VNC computing technology, creating the appearance of a legitimate login session from the victim’s own computer. This sophisticated method allows the attacker to conduct unauthorized transactions without triggering any security alerts, as the bank’s systems only detect what seems to be normal activity using the correct credentials.
Distinguish malware sent via WeTransfer
Raising awareness of cybersecurity risks and promoting the responsible use of electronic services are crucial measures for safeguarding both individuals and institutions from cyber threats. When engaging in data transfer via platforms like WeTransfer, adhering to a set of straightforward guidelines can significantly enhance security:
- Expectation vs. Reality: If you receive files unexpectedly, proceed with caution. Unsolicited files can often be a red flag for phishing attempts or malware distribution.
- Verify the Sender: Always confirm the identity of the sender. Check the sender’s email address to ensure it matches the individual or organization you recognize. Discrepancies in the email address could indicate a fraudulent attempt to impersonate a trusted contact.
- Consistency in Sender Details: Even if the sender’s name appears familiar, a mismatched email address is a cause for concern. Ensure that the email address aligns with the sender’s known contact information.
- Size Matters: Be wary of files that are unusually small, especially if they are in the kilobyte (KB) range. Such files could potentially be malicious payloads disguised as harmless documents.
- Scrutinize Links:** Examine any links contained in the email. Be cautious if the link appears strange, excessively long, or directs you to a website other than WeTransfer. Cybercriminals often use deceptive links to trick recipients into visiting malicious sites or downloading harmful files.
By staying vigilant and adhering to these guidelines, users can significantly reduce their vulnerability to cyber threats and ensure a safer online experience when using file transfer services like WeTransfer.
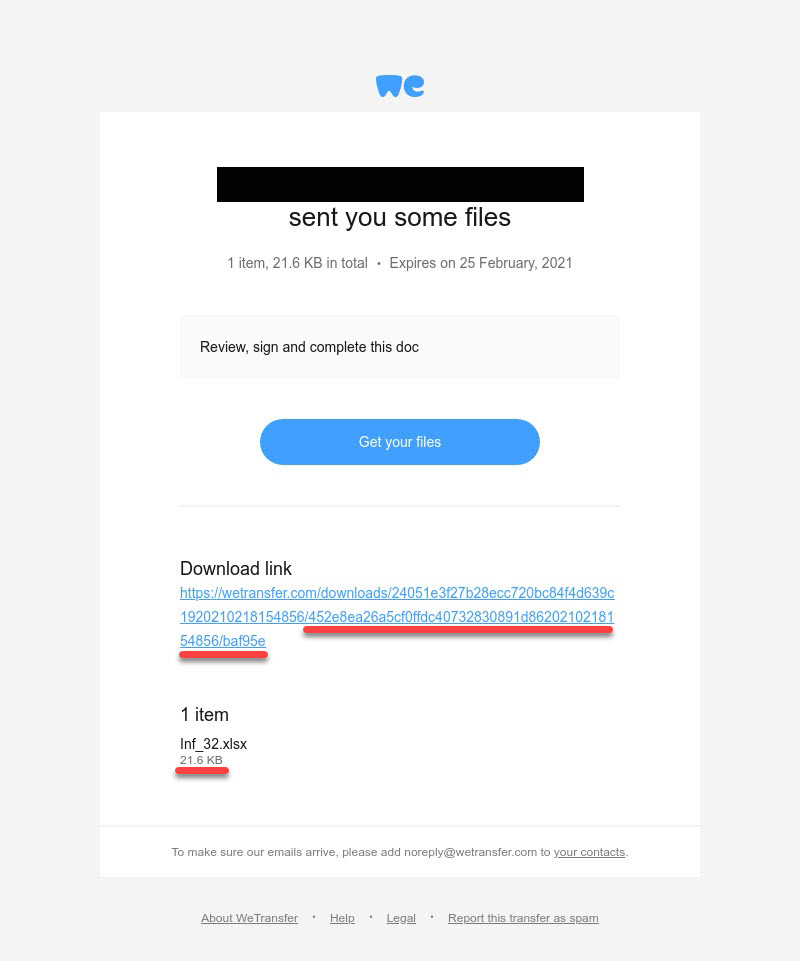
Example of a fraudulent link
hxxps://wetransfer[.] com/downloads/52d55eeb42591d9ebbffe5326326858320210218183005/8b80cbbd9c1b8f7695b8de69e995ebee20210218183005/8c0cd5utm_campaign=WT_email_tracking&utm_content=general&utm_medium=download_button&utm_source=notify_recipient_email
Note: https has been replaced by hxxps and .com by [.] com to avoid activating the link and making it usable or detectable by antiviruses.
How to protect yourself while loading from WeTransfer
- Verify Unexpected Files: Do not open files that you were not expecting or if you do not recognize the sender. If the files come from someone you know but were unexpected or unsolicited, reach out to the sender to confirm their authenticity.
- Be Cautious with Small Files: Exercise caution when receiving small files, regardless of their format (e.g., Docx, Xlsx, PDF, JPG). These could potentially contain malicious payloads.
- Check the Sender’s Email Address: Always verify the sender’s email address. Be especially wary if there are additional email addresses included in the CC or BCC fields. WeTransfer does not send copies, so this could be a sign of a phishing attempt.
- Beware of Service Name Changes: If you are a paid WeTransfer subscriber and receive an email referring to “WeTransfer Plus,” be aware that the service has been renamed to “WeTransfer Pro.” Any communication using the old name may be suspicious.
- Ignore Requests for Email and Password: If a file download prompts you for your email and password, do not proceed unless you are certain the file is password-protected and this is a legitimate security measure. Verify with the sender if necessary.
- Disregard Phone Support Claims: WeTransfer does not provide technical support over the phone. Any calls claiming to represent WeTransfer’s technical support should be treated as fraudulent.
- Maintain Up-to-Date Antivirus Software: Ensure that you have reliable antivirus software installed on your computer and that it is regularly updated to protect against the latest threats.
By following these guidelines, you can enhance your security and reduce the risk of falling victim to cyber threats while using WeTransfer for file downloads.
References
Surge in ZLoader Attacks Observed | PhishLaps
https://info.phishlabs.com/blog/surge-in-zloader-attacks-observed
ZLoader Dominates Email Payloads in Q1 | PhishLaps
https://info.phishlabs.com/blog/zloader-dominates-email-payloads-in-q1
Alert (AA21-076A) | CISA
https://us-cert.cisa.gov/ncas/alerts/aa21-076a
TrickBot Malware | CISA
https://us-cert.cisa.gov/sites/default/files/publications/AA21-076A-TrickBot_Malware_508.pdf
Zloader | Any.run
How to recognize malicious files which are spam | WeTransfer
Phishing attempts and other weird WeTransfer imitations | WeTransfer
How to recognize malicious files which are spam | WeTransfer

